Most Dangerous Cyber Threats Impacting Businesses Today
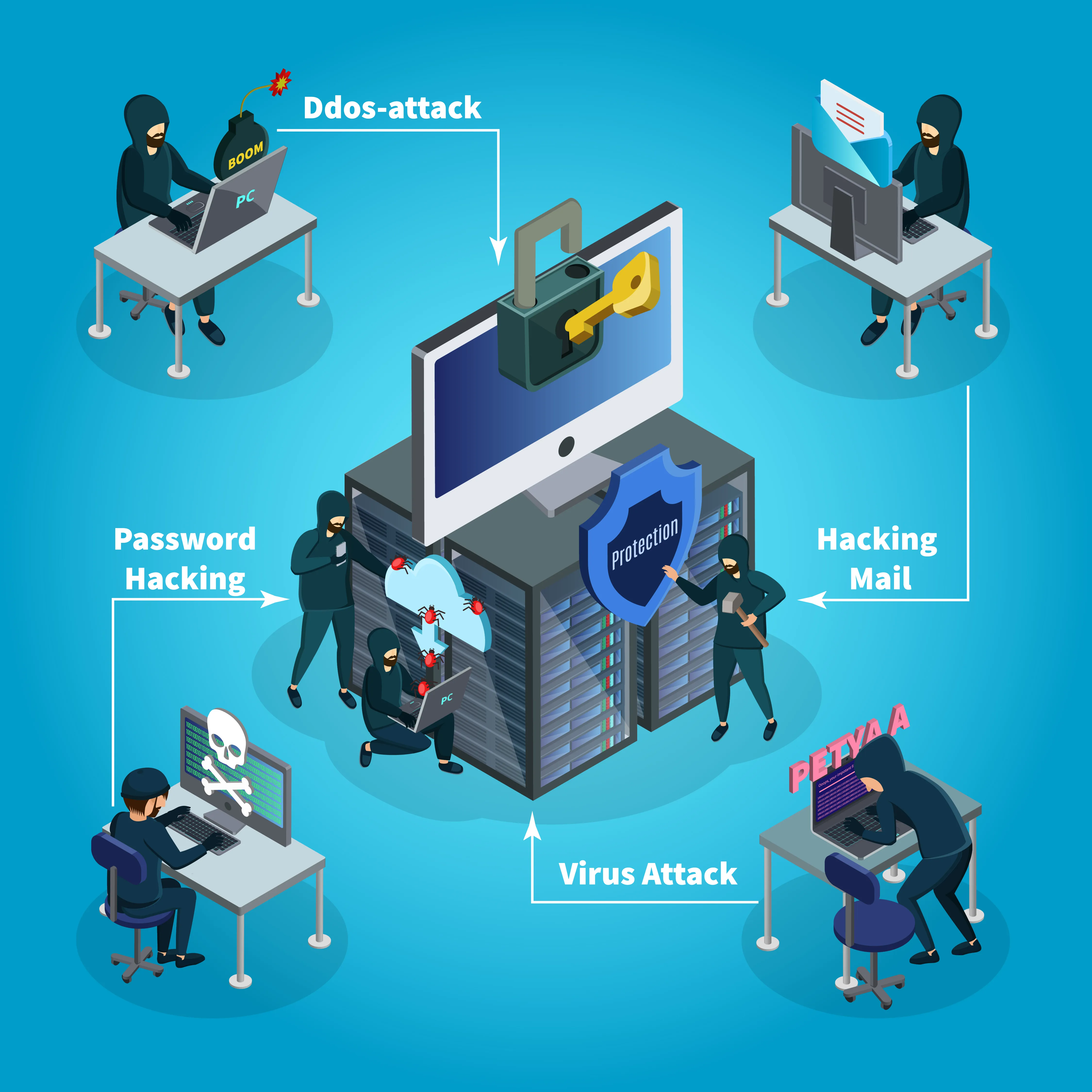
In the digital day and age, gaining customers and ensuring their products and services are successful are not the only things companies have to worry about. Unfortunately, with the advancement of technology and ever since remote work has become more common in the wake of the COVID-19 pandemic, cyberattacks are on the rise, with many companies affected by cyberattacks.
Companies are now even more vulnerable to getting targeted with cyberattacks because cybercriminals have started growing even more competent when stealing and compromising the company's sensitive and confidential data. In this guide, we will explore the most common cyber attacks that affect businesses today and what steps they can take to ensure their data remains safe and secure, so without further ado, let's get started.
Why Do Businesses Need To Protect Their Data & Privacy?
There are various reasons why companies need to protect their data from cyber attacks, as failure to do so can lead to severe consequences:
1) Data Protection
Cyber attacks often target sensitive data like customer, financial, and intellectual property. Safeguarding against these attacks can help companies protect their sensitive and confidential data against theft, destruction, and manipulation.
Identifying ransomware threats involves actively monitoring the company's defenses and analyzing recent incidents for insights. Antivirus software and a web application firewall help prevent malicious email attachments and minimize ransomware exposure.
2) Financial Loss Prevention
Cyber attacks can result in severe financial loss for companies. This is due to theft of funds, business disruption, and other regulatory fines. Protection against these attacks allows companies to mitigate the risk of financial loss to the business.
3) Protecting Reputation
A successful cyber attack can hinder a business's reputation, which leads to a loss of trust from customers, stakeholders, and partners. By offering protection against cyber attacks, companies can maintain their reputation and credibility.
4) Protecting Customer Trust
Customers are a significant factor that helps propel a company towards major success. Failure to protect your customers from cyber-attacks and compromising their sensitive and confidential data can lead to a lack of trust from your customers, and you'll ultimately lose them. Protecting your customers from cyber threats helps maintain customer trust and loyalty.
5) Compliance Requirements
Many industries have compulsory regulatory requirements regarding data security and privacy. Failure to protect themselves and their customers and employees against cyber threats can lead to non-compliance with these regulations and result in legal consequences and financial penalties.
6) Preventing Data Breaches
Data breaches can lead to financial loss, reputational damage, and other legal liabilities. Protecting data using various methods like encryption, access controls, and other effective security measures can help prevent data breaches.
What Are The Top 5 Cyber Threats Businesses Are Facing Today?
These are some of the most common cyber threats plaguing businesses today. These include:
1) Malware Attacks
Malware attacks are common cyber attacks that can be very dangerous for companies. Malware attacks are malicious codes or software like viruses, worms, trojans, ransomware, and spyware. Once the person's devices are infected with Malware, the cybercriminal can gain unauthorized access to the victim's personal information and financial data, which the hacker can use for identity theft and other fraudulent purposes.
2) Phishing Scams
Phishing scams have become common among companies, with cybercriminals using social engineering tactics to trick users into divulging sensitive and confidential data. In companies, phishing scams happen where the cybercriminal will pretend to be higher-up from the company, a part of management, or someone the user trusts.
They usually craft a fake email and urge the person to click the email link or attachments. Unfortunately, once the user clicks on the link and attachments, it's too late, and the cybercriminal has gained access to the company's confidential and sensitive documents.
3) SQL Injection Attacks
SQL injection attacks exploit vulnerabilities in web applications by inserting malicious SQL code into the input fields. This enables attackers to manipulate and exploit databases, steal data, or execute unauthorized commands.
4) Insider Threats
Insider threats are cyber threats that are coming from within the organization. They occur when individuals within an organization exploit their access privileges to steal data and sabotage systems.
Insider threats can be caused by anyone, from employees to contractors and even business partners. These people can access sensitive and confidential data that they use to damage the company's reputation and steal sensitive data.
5) DoS and DDoS Attacks
Denial of Service (DoS) and Distributed Denial of Service (DDoS) Attacks can overwhelm the company's system, network, or traffic with excessive traffic, which will cause it to become unavailable to legitimate users. These attacks can also disrupt business operations and create financial losses. DoS Attacks are often used to force companies to pay a ransom to regain access to the company website or their data.
How Can Businesses Protect Themselves Against Cyber Threats?
There are various ways through which businesses can protect themselves from cyber-attacks. Some of the most effective methods that they can implement include:
1) Using A Business VPN
Investing in a Secure Business VPN is one of the most effective ways companies can keep their sensitive and confidential data safe and secure from interception. A VPN (Virtual Private Network) masks your IP address and encrypts your internet traffic, ensuring that cyber criminals and other malicious actors cannot decipher and intercept the company's sensitive documents.
A secure access VPN is beneficial when the company is primarily operating remotely. It provides contractors, employees, and partners with secure remote access to corporate networks and resources. All data transmitted over the VPN connection uses robust encryption protocols like SSL/TLS, ensuring malicious third parties cannot intercept sensitive information.
2) Use IP-Based Insights to Strengthen Security
In addition to using a secure VPN, companies can benefit from using IP intelligence solutions like IPinfo, which provides geolocation data for personalization and security. This helps businesses monitor access patterns, detect unusual login locations, block known proxy or VPN IPs, and enforce geo-based access restrictions. By verifying IP origins and analyzing regional behaviors, businesses can strengthen their defense mechanisms and reduce the risk of unauthorized access and fraudulent activity.
3) Conduct Regular Security Audits
The company should conduct regular security audits and penetration testing, implement robust threat hunting techniques, and perform periodic vulnerability assessments to identify and address security weaknesses and gaps in defenses. Additionally, it should utilize automated tools and engage with third-party security experts when necessary.
4) Employee Training & Awareness
Employees should be provided comprehensive training on the best cybersecurity practices, identifying phishing emails, creating strong and complex passwords, and identifying and recognizing social engineering tactics. Companies should regularly reinforce awareness through various training sessions and security updates.
5) Strong Password & Two Factor Authentication
Employees and business management should encourage using strong and complex passwords so that malicious actors cannot quickly gain unauthorized access to sensitive company data. The password should be complex and not that easy to guess. A strong password consists of an uppercase letter, lowercase letter, special characters, and numbers.
The company should also enable two-factor authentication on all of its online accounts. 2FA is an additional security measure that requires you to enter an extra verification step before you are allowed to gain access to your online accounts. This is particularly useful for companies where only authorized personnel can access the company's online accounts, and it would become challenging for cyber criminals to intercept the company's online accounts that contain sensitive data.
Regular security audits, secure VPNs, and leveraging IT management services are key steps businesses can take to safeguard their operations against cyber threats.
Conclusion
Cyber threats are on the rise, and while it may be a cause of concern for companies since their sensitive and confidential data, as well as the data of their employees and customers, may be at risk, there are luckily ways to reduce the impacts of some of the common cyber threats that companies have to face. Investing in a secure access VPN and opting for other measures like training employees on the best cybersecurity practices is a simple way to prevent companies from falling victim to cyber-attacks like malware and phishing attacks.